Difference between revisions of "Gameplay"
| (50 intermediate revisions by the same user not shown) | |||
| Line 7: | Line 7: | ||
<div class="tablenotes"> | <div class="tablenotes"> | ||
<h3>Page Source</h3> | <h3>Page Source</h3> | ||
| + | <div class="fadediv2"></div> | ||
| + | <div class="articleimg" style="float:right; margin: 1em; margin-top: 0px; margin-right:0px;"><html><a href="http://johnisdead.withinhubris.com/images/4/4d/Viewsource.png" target="_blank"><img src="http://johnisdead.withinhubris.com/images/4/4d/Viewsource.png" alt="" /></a></html><p style="margin-bottom:0px; text-align:left;"><i>The source code of a page on Johnisdead.com referencing the page's title, image and audio files, and a hidden comment.</i></p></div> | ||
<p>Most browsers have the option view the source of any web-page on the internet. This will reveal the page's HTML as loaded by your browser. Viewing a page's HTML will not only allow you to easily view <b>secret links</b> and <b>filenames</b>, but it will also reveal <b>comments</b> - text hidden within a page's source code. Viewing a page's source is also the easiest way to uncover the names and details of any <b>scripts</b> referenced on the page.</p> | <p>Most browsers have the option view the source of any web-page on the internet. This will reveal the page's HTML as loaded by your browser. Viewing a page's HTML will not only allow you to easily view <b>secret links</b> and <b>filenames</b>, but it will also reveal <b>comments</b> - text hidden within a page's source code. Viewing a page's source is also the easiest way to uncover the names and details of any <b>scripts</b> referenced on the page.</p> | ||
<h3>Page Title</h3> | <h3>Page Title</h3> | ||
| + | <div class="fadediv2"></div> | ||
<p>The <b>page title</b> is the text that appears within your browser's tabs, favorites, and history. These titles often contain hints or ciphers that should be documented.</p> | <p>The <b>page title</b> is the text that appears within your browser's tabs, favorites, and history. These titles often contain hints or ciphers that should be documented.</p> | ||
<h3>Files</h3> | <h3>Files</h3> | ||
| + | <div class="fadediv2"></div> | ||
<p>Most pages will contain <b>image and audio files</b>. Accessing these files through the page source is beneficial not only for documentation purposes, but also because said files may not be fully implemented into a page. For example, a page may be scripted to only play the first five seconds of a ten second audio file. Accessing the page's files directly will reveal any hidden details. Analyzing files further will be covered in more detail further down.</p> | <p>Most pages will contain <b>image and audio files</b>. Accessing these files through the page source is beneficial not only for documentation purposes, but also because said files may not be fully implemented into a page. For example, a page may be scripted to only play the first five seconds of a ten second audio file. Accessing the page's files directly will reveal any hidden details. Analyzing files further will be covered in more detail further down.</p> | ||
</div> | </div> | ||
| Line 18: | Line 22: | ||
<h2>Solving Ciphers</h2> | <h2>Solving Ciphers</h2> | ||
<p>Nearly every aspect of Johnisdead's gameplay will at some point involve ciphers. Ciphers are coded messages that must be translated in a specific way to solve. There are a multitude of different ciphers, each requiring their own methods to solve: | <p>Nearly every aspect of Johnisdead's gameplay will at some point involve ciphers. Ciphers are coded messages that must be translated in a specific way to solve. There are a multitude of different ciphers, each requiring their own methods to solve: | ||
| − | <div class="tablenotes"> | + | <div class="tablenotes mw-collapsible mw-collapsed"> |
| + | <p style="display:inline;"> | ||
| + | <b style="font-size: 1.1em; text-shadow: 0 0 5px gold;"> | ||
| + | Ascii / Decimal Based Cipher Guide | ||
| + | </b> | ||
| + | </p> | ||
| + | <div class="mw-collapsible-content"> | ||
<h3>Binary Ciphers</h3> | <h3>Binary Ciphers</h3> | ||
| − | <p><b>Binary ciphers</b> are groups of eight | + | <div class="fadediv2"></div> |
| + | <p><b>Binary ciphers</b> are series of ones and zeros in groups of eight. Every letter, number, and punctuation mark has a specific binary code that it is represented by. For example, the capitalized letter "A" is referenced by the binary code "01000001". The number one is referenced by the binary code "00110001". Sometimes entire sentences are encoded in binary, resulting in long blocks of binary code.</p> | ||
<div class="textexampletitle"> | <div class="textexampletitle"> | ||
| − | <p style="padding-left: 1em; padding-bottom: 0.5em; color: yellow; margin-bottom: 0px;"> | + | <p style="padding-left: 1em; padding-bottom: 0.5em; color: yellow; margin-bottom: 0px;">Binary Cipher Examples</p> |
</div> | </div> | ||
<div class="textexamplebox"><poem style="margin-top: 0px; padding-top: 10px;"> | <div class="textexamplebox"><poem style="margin-top: 0px; padding-top: 10px;"> | ||
| − | + | 01000010 01100001 01110011 01101001 01100011 00100000 01000010 01101001 01101110 01100001 01110010 01111001 | |
| − | <span class="solution"> | + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Basic Binary</span> |
| + | <b style="margin-left:2em;">Solution:</b> Solve cipher through any basic binary translator. | ||
| + | <br /> | ||
| + | 10011110 01001110 10000110 01110110 10010110 01000010 00000100 00100110 10100110 11001110 01001110 10100110 01101110 10100110 01001010 | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Reversed Binary</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Reverse the cipher and solve. | ||
| + | <br /> | ||
| + | ABABAABA ABBAABAB ABBBAAAA ABBABBAA ABBAAAAB ABBAAABB ABBAABAB ABBAABAA AABAAAAA ABAAAABA ABBABAAB ABBABBBA ABBAAAAB ABBBAABA ABBBBAAB | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Replaced Binary</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Replace the letters "A" and "B" with zeroes and ones respectively and solve. | ||
| + | </poem></div> | ||
| + | <div class="summary" style="background-color:black;"> | ||
| + | <ul style="margin-top: 0px;"> | ||
| + | <li> | ||
| + | <b>Identify</b>: Groups of eight characters consisting of either ones or zeroes. | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tool</b>: Any basic binary translator - [https://paulschou.com/tools/xlate/ Link] | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: Binary representing common characters begin with the number zero. If you encounter binary that begins with the number one, it's likely that the entire cipher has been reversed. In this case, one must correct the cipher by reversing it themselves for it to be solved. | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: As its name implies, binary's most defining trait is its use of only two characters. This makes it easily identifiable. You may encounter some binary ciphers where the ones and zeroes have been replaced with letters or even entire words. If you encounter a strange looking cipher consisting of patters such as "ABAAAAAB", its likely an obscured binary cipher. | ||
| + | </li> | ||
| + | </ul> | ||
| + | </div> | ||
| + | <br /> | ||
| + | <h3>Octal Ciphers</h3> | ||
| + | <div class="fadediv2"></div> | ||
| + | <p><b>Octal ciphers</b> are fairly similar to binary ciphers. Both ciphers consist of numbers and often appear in groups of eight. However, octal is a bit more complicated than binary. Octal is the "base-8" number system, meaning it uses combinations of the numbers zero through seven to represent characters.</p> | ||
| + | |||
| + | <div class="textexampletitle"> | ||
| + | <p style="padding-left: 1em; padding-bottom: 0.5em; color: yellow; margin-bottom: 0px;">Octal Cipher Examples</p> | ||
| + | </div> | ||
| + | <div class="textexamplebox"><poem style="margin-top: 0px; padding-top: 10px;"> | ||
| + | 20460563 32261440 23661564 302660 | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Basic Octal</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Solve cipher through any basic octal translator. | ||
| + | <br /> | ||
| + | 066203 46516632 04026213 36117213 66526442 | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Reversed Octal</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Reverse the cipher and solve. | ||
| + | </poem></div> | ||
| + | <div class="summary" style="background-color:black;"> | ||
| + | <ul style="margin-top: 0px;"> | ||
| + | <li> | ||
| + | <b>Identify</b>: Groups of numbers ranging from zero to seven. These groups never exceed eight characters. Unlike binary, these groups may contain less than eight characters. | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tool</b>: Any basic octal translator - [https://paulschou.com/tools/xlate/ Link] | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: The maximum amount of numbers that may appear in an octal cipher before a space appears is eight. This makes octal ciphers fairly easy to identify. If you encounter a cipher consisting of eight numbers followed by a smaller group of numbers, then it is likely an octal cipher. Example: "23240524 250". | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: The numbers within an octal cipher never exceed seven. If you see numbers higher than seven in a cipher, then it is not an octal code. | ||
| + | </li> | ||
| + | </ul> | ||
| + | </div> | ||
| + | <br /> | ||
| + | <h3>Hexadecimal Ciphers</h3> | ||
| + | <div class="fadediv2"></div> | ||
| + | <p><b>Hexadecimal ciphers</b> are fairly easy to identify. Whereas binary and octal ciphers were both made up of groups of eight characters, hexadecimal ciphers are made up of groups of two characters. These two characters will either be two numbers, or a number followed by a letter. While octal uses a "base-8" system, hexadecimal uses a "base-16" system. This means that hexadecimal uses 16 characters - the numbers zero through nine and the letters "A" through "F".</p> | ||
| + | |||
| + | <div class="textexampletitle"> | ||
| + | <p style="padding-left: 1em; padding-bottom: 0.5em; color: yellow; margin-bottom: 0px;">Hexadecimal Cipher Examples</p> | ||
| + | </div> | ||
| + | <div class="textexamplebox"><poem style="margin-top: 0px; padding-top: 10px;"> | ||
| + | 42 61 73 69 63 20 48 65 78 61 64 65 63 69 6d 61 6c | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Basic Hexadecimal</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Solve cipher through any basic hexadecimal translator. | ||
| + | <br /> | ||
| + | c6 16 d6 96 36 56 46 16 87 56 84 02 46 56 37 27 56 67 56 25 | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Reversed Hexadecimal</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Reverse the cipher and solve. | ||
| + | </poem></div> | ||
| + | <div class="summary" style="background-color:black;"> | ||
| + | <ul style="margin-top: 0px;"> | ||
| + | <li> | ||
| + | <b>Identify</b>: Groups of two characters consisting of either two numbers or a number followed by a letter. Only the numbers zero through nine and the letters "A" through "F" are used. | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tool</b>: Any basic hexadecimal translator - [https://paulschou.com/tools/xlate/ Link] | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: Hexadecimal is a very distinct code. If you encounter any oddities such as groups of three characters or numbers and letters outside of the hexadecimal range, then the code has either been tampered or is a completely different cipher completely. | ||
| + | </li> | ||
| + | </ul> | ||
| + | </div> | ||
| + | <br /> | ||
| + | <h3>Base32 Ciphers</h3> | ||
| + | <div class="fadediv2"></div> | ||
| + | <p>As the name implies, <b>Base32 ciphers</b> utilize the "base-32" system. This means that Base32 ciphers will only ever contain the following 32 characters - the capitalized letters "A" through "Z" and the numbers two through seven. Base32 ciphers contain no spaces. This makes them fairly easy to identify, as they often appear as long, uninterrupted blocks of text consisting of numbers and capitalized letters.</p> | ||
| + | |||
| + | <div class="textexampletitle"> | ||
| + | <p style="padding-left: 1em; padding-bottom: 0.5em; color: yellow; margin-bottom: 0px;">Base32 Cipher Examples</p> | ||
| + | </div> | ||
| + | <div class="textexamplebox"><poem style="margin-top: 0px; padding-top: 10px;"> | ||
| + | IJQXG2LDEBBGC43FGMZA | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Basic Base32</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Solve cipher through any basic Base32 translator. | ||
| + | <br /> | ||
| + | SZMKWZFMCCIIWSNOSLZMXSJK | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Reversed Base32</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Reverse the cipher and solve. | ||
</poem></div> | </poem></div> | ||
| + | <div class="summary" style="background-color:black;"> | ||
| + | <ul style="margin-top: 0px;"> | ||
| + | <li> | ||
| + | <b>Identify</b>: Long strings of text consisting of capitalized letters and the numbers two through seven. Contains no spaces. | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tool</b>: Any basic base32 translator - [https://paulschou.com/tools/xlate/ Link] | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: Base32 follows a strict character set. If you are having trouble solving a base32 cipher, make sure that there are no lower-case letters, spaces, or instances of the numbers zero, one, eight, or nine. Also ensure that your entire code is on a single line, as your base32 translator may be interpreting the line break as a character within the code. | ||
| + | </li> | ||
| + | </ul> | ||
| + | </div> | ||
| + | <br /> | ||
| + | <h3>Base64 Ciphers</h3> | ||
| + | <div class="fadediv2"></div> | ||
| + | <p><b>Base64 ciphers</b> utilize the "base-64" system, meaning they may consist of any letter, upper and lower-case, and any number. Base64 ciphers may also include the characters "/" and "+". Base64 ciphers sometimes end with one or two equal signs. There are also no spaces in Base64 ciphers, making them distinct blocks of what initially appears to be garbled letters and numbers.</p> | ||
| + | |||
| + | <div class="textexampletitle"> | ||
| + | <p style="padding-left: 1em; padding-bottom: 0.5em; color: yellow; margin-bottom: 0px;">Base64 Cipher Examples</p> | ||
| + | </div> | ||
| + | <div class="textexamplebox"><poem style="margin-top: 0px; padding-top: 10px;"> | ||
| + | QmFzaWMgQmFzZTY0 | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Basic Base64</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Solve cipher through any basic Base64 translator. | ||
| + | <br /> | ||
| + | TW9yZSBCYXNlNjQgQ29kZQ== | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">More Base64 Code</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Solve cipher through any basic Base64 translator. | ||
| + | <br /> | ||
| + | =UGZvNEI0YTZzFmQgQWZzJXZ2VmU | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Reversed Base64 Code</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Reverse the cipher and solve. | ||
| + | </poem></div> | ||
| + | <div class="summary" style="background-color:black;"> | ||
| + | <ul style="margin-top: 0px;"> | ||
| + | <li> | ||
| + | <b>Identify</b>: Long strings of text consisting of upper and lower-case letters, numbers, and the characters "/" and "+". Often ends with one or two equal signs. | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tool</b>: Any basic base64 translator - [https://paulschou.com/tools/xlate/ Link] | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: Unlike previous ciphers, base64 contains all letters and numbers. This in and of itself makes it fairly easy to identify. | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: The equal signs that sometimes appear within base64 ciphers always appear at the end of the code. If you encounter a cipher with one or two equal signs at the beginning of the text, it's likely this is a base64 cipher that has been reversed. | ||
| + | </li> | ||
| + | </ul> | ||
| + | </div> | ||
| + | <br /> | ||
| + | <h3>Ascii85 Ciphers</h3> | ||
| + | <div class="fadediv2"></div> | ||
| + | <p><b>Ascii85 ciphers</b> utilize the "base-85" system. As you might expect, this means that Ascii85 codes consist of 85 different characters. The characters used in Ascii85 ciphers are the Ascii characters 33 through 117. What this means exactly is that Ascii85 ciphers will contain every upper-case letter, every number, a plethora of punctuation marks and symbols such as "#" and "$", and the lower-case letters "a" through "u". Despite their intimidating appearance, Ascii85 ciphers can be solved the same as any other.</p> | ||
| + | |||
| + | <div class="textexampletitle"> | ||
| + | <p style="padding-left: 1em; padding-bottom: 0.5em; color: yellow; margin-bottom: 0px;">Ascii85 Cipher Examples</p> | ||
| + | </div> | ||
| + | <div class="textexamplebox"><poem style="margin-top: 0px; padding-top: 10px;"> | ||
| + | 6=FqL@j"'Y@qfX:2# | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Basic Ascii85</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Solve cipher through any basic Ascii85 translator. | ||
| + | <br /> | ||
| + | 9lG&`+@C'aE,95u@<?'k+@1'YBk]Oa | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">More Complicated Ascii85</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Solve cipher through any basic Ascii85 translator. | ||
| + | <br /> | ||
| + | aO]kBY'1@+&fYcE_#tI; | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Reversed Ascii85 Code</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Reverse the cipher and solve. | ||
| + | </poem></div> | ||
| + | <div class="summary" style="background-color:black;"> | ||
| + | <ul style="margin-top: 0px;"> | ||
| + | <li> | ||
| + | <b>Identify</b>: Long, chaotic strings of text consisting of any upper-case letter, any number, a myriad of symbols, and any lower-case letter from "a" through "u". | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tool</b>: Any basic Ascii85 translator - [https://paulschou.com/tools/xlate/ Link] | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: Ascii85 ciphers are incredibly chaotic, containing many different characters. This makes them easy to identify. | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: Ascii85 ciphers are often found split between multiple lines. If you encounter multiple lines of Ascii85 code that is translating incorrectly, you may need to place the separate codes on one single line. | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: There is no easily discernible way to tell if an Ascii85 cipher has been reversed or not. Unfortunately, a fair amount of experimentation may be required to solve some Ascii85 ciphers. | ||
| + | </li> | ||
| + | </ul> | ||
| + | </div> | ||
| + | <br /> | ||
| + | <h3>Decimal / Character / Ascii Ciphers</h3> | ||
| + | <div class="fadediv2"></div> | ||
| + | <p><b>Decimal ciphers</b> hide messages by directly referencing the Ascii value of each encoded character. Every character has an Ascii value attached to it often referred to as a decimal. Decimal ciphers simply consist of the values of each character of the encoded message separated by a space.</p> | ||
| + | |||
| + | <div class="textexampletitle"> | ||
| + | <p style="padding-left: 1em; padding-bottom: 0.5em; color: yellow; margin-bottom: 0px;">Decimal Cipher Examples</p> | ||
| + | </div> | ||
| + | <div class="textexamplebox"><poem style="margin-top: 0px; padding-top: 10px;"> | ||
| + | 66 97 115 105 99 32 68 101 99 105 109 97 108 | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Basic Decimal</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Solve cipher through any basic Decimal translator. | ||
| + | <br /> | ||
| + | 801 79 901 501 99 101 86 23 001 101 511 411 101 811 101 28 | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Reversed Decimal</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Reverse the cipher and solve. | ||
| + | </poem></div> | ||
| + | <div class="summary" style="background-color:black;"> | ||
| + | <ul style="margin-top: 0px;"> | ||
| + | <li> | ||
| + | <b>Identify</b>: One, two, or three digit numbers separated by spaces. Decimal ciphers contain no letters and only span from the number zero to 127. | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tool</b>: Any basic Decimal translator - [https://paulschou.com/tools/xlate/ Link] | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: Decimal ciphers look fairly similar to hexadecimal ciphers. The main difference between the two is that decimal ciphers lack letters. | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: Because 127 is the maximum valid ascii value, decimal ciphers will not contain numbers above 127. If any number above this is encountered in a cipher, the cipher is either decimal code that needs to be reversed, a decimal cipher that has been tampered with, or a completely different cipher completely. | ||
| + | </li> | ||
| + | </ul> | ||
| + | </div> | ||
| + | <br /> | ||
| + | </div> | ||
| + | </div> | ||
<div class="summary"> | <div class="summary"> | ||
| + | <ul style="margin-top: 0px; padding-top: 0.5em;"> | ||
| + | <li> | ||
| + | Click "<b>Expand</b>" for a guide covering various Ascii and Decimal-based ciphers. | ||
| + | </li> | ||
| + | </ul> | ||
| + | </div> | ||
| + | <br /> | ||
| + | <div class="tablenotes mw-collapsible mw-collapsed"> | ||
| + | <p style="display:inline;"> | ||
| + | <b style="font-size: 1.1em; text-shadow: 0 0 5px gold;"> | ||
| + | Text Based Cipher Guide | ||
| + | </b> | ||
| + | </p> | ||
| + | <div class="mw-collapsible-content"> | ||
| + | <h3>Caesar Ciphers</h3> | ||
| + | <div class="fadediv2"></div> | ||
| + | <p><b>Caesar shifts</b> are simple ciphers that consist of messages written with altered alphabets. The alphabets used in Caesar ciphers have different starting points depending on the shift used. For example, a Caesar shift of zero would use our normal alphabet beginning with "A", whereas a Caesar shift of five would use an alphabet that begins with the letter "F".</p> | ||
| + | |||
| + | <div class="textexampletitle"> | ||
| + | <p style="padding-left: 1em; padding-bottom: 0.5em; color: yellow; margin-bottom: 0px;">Caesar Cipher Examples</p> | ||
| + | </div> | ||
| + | <div class="textexamplebox"><poem style="margin-top: 0px; padding-top: 10px;"> | ||
| + | Gfxnh Hfjxfw Hnumjw | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Basic Caesar Cipher</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Solve cipher through any basic Caesar translator. | ||
| + | <br /> | ||
| + | wjmunH wfxjfH ijxwjajW | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Reversed Caesar Cipher</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Reverse the cipher and solve. | ||
| + | </poem></div> | ||
| + | <div class="summary" style="background-color:black;"> | ||
| + | <ul style="margin-top: 0px;"> | ||
| + | <li> | ||
| + | <b>Identify</b>: Text or sentences that often use proper capitalization and grammar but consist of garbled text. | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tool</b>: Any basic Caesar translator - [http://rumkin.com/tools/cipher/caesar.php Link] | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: There's no easy way of discerning which shift a Caesar cipher is using. The best way to solve a Caesar cipher is to type them into a Caesar cipher translator and cycle through the different shifts to discover the correct one. | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: Some Caesar ciphers are reversed. This can make solving them tricky as it will be more difficult to notice the translated words once the correct shift is uncovered. If you notice any oddities within the Caesar cipher such as punctuation appearing at the beginning of sentences or capitalized letters appearing at the end, the cipher is most likely reversed. | ||
| + | </li> | ||
| + | </ul> | ||
| + | </div> | ||
| + | <br /> | ||
| + | <h3>Keyed Caesar Ciphers</h3> | ||
| + | <div class="fadediv2"></div> | ||
| + | <p><b>Keyed Caesar ciphers</b> are Caesar ciphers that have had their shifted alphabets further altered by a keyword or phrase. The key used in keyed Caesar ciphers is placed at the front of the alphabet. For example, an alphabet with no shifts using the key "JID" would be "JIDABCEFGHKLMN (...)". The shift is then applied to these keyed alphabets, making them nearly impossible to solve through simple guesswork. | ||
| + | </p> | ||
| + | |||
| + | <div class="textexampletitle"> | ||
| + | <p style="padding-left: 1em; padding-bottom: 0.5em; color: yellow; margin-bottom: 0px;">Keyed Caesar Cipher Examples</p> | ||
| + | </div> | ||
| + | <div class="textexamplebox"><poem style="margin-top: 0px; padding-top: 10px;"> | ||
| + | Rglojb Ibxba Ykbrkq | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Simple Keyed Caesar</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Shift the Caesar cipher by zero and use the key "KEY". | ||
| + | <br /> | ||
| + | Oezyxqi Wqjqp Omqcmb | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">Complex Keyed Caesar</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Shift the Caesar cipher by 13 and use the key "KEY". | ||
| + | </poem></div> | ||
| + | <div class="summary" style="background-color:black;"> | ||
<ul style="margin-top: 0px;"> | <ul style="margin-top: 0px;"> | ||
<li> | <li> | ||
| − | <b>Identify</b>: | + | <b>Identify</b>: The same as regular Caesar ciphers - words or sentences usually containing correct punctuation and grammar consisting of gibberish. Distinguishable from normal Caesar ciphers simply in the fact that they cannot be solved from shifts alone, requiring a key. |
| + | </li> | ||
| + | <li> | ||
| + | <b>Tool</b>: Any basic keyed Caesar translator - [http://rumkin.com/tools/cipher/caesar-keyed.php Link] | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: Brute-forcing a keyed Caesar cipher is incredibly difficult. When encountering a difficult keyed Caesar cipher, search for any nearby clues or relevant words that may be used as a key. | ||
| + | </li> | ||
| + | </ul> | ||
| + | </div> | ||
| + | <br /> | ||
| + | <h3>Vigenere Ciphers</h3> | ||
| + | <div class="fadediv2"></div> | ||
| + | <p><b>Vigenere ciphers</b> can be thought of as a more complicated from of Caesar ciphers. While Caesar ciphers used a single shifted alphabet, Vigenere ciphers are encoded with multiple alphabets with varying starting positions. The starting position of these alphabets are determined by a keyword or phrase, with each letter in the key being the starting letter used for the alphabets of each letter in the cipher. Vigenere ciphers are more easily explained through example:</p> | ||
| + | |||
| + | <div class="textexampletitle"> | ||
| + | <p style="padding-left: 1em; padding-bottom: 0.5em; color: yellow; margin-bottom: 0px;">Vigenere Cipher Examples</p> | ||
| + | </div> | ||
| + | <div class="textexamplebox"><poem style="margin-top: 0px; padding-top: 10px;"> | ||
| + | <span class="solution">Key:</span> "CAT" | ||
| + | <span class="solution">Cipher:</span> "DOG" | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">BON</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Solve cipher through any basic Vigenere translator using the key "CAT". | ||
| + | |||
| + | <b style="margin-left:2em;">Explanation:</b> Each letter in the cipher "DOG" uses its own alphabet that begins with the corresponding letter in the key "CAT". | ||
| + | |||
| + | 1--2--3--4--5--6--7--8--9--10-11-12-13-14-15-16-17-18-19-20-21-22-23-24-25-26 | ||
| + | <b>C</b>--D--E--F--G--H--I--J--K--L--M--N--O--P--Q--R--S--T--U--V--W--X--Y--Z--A--B | ||
| + | <b>A</b>--B--C--D--E--F--G--H--I--J--K--L--M--N--O--P--Q--R--S--T--U--V--W--X--Y--Z | ||
| + | <b>T</b>--U--V--W--Z--Y--Z--A--B--C--D--E--F--G--H--I--J--K--L--M--N--O--P--Q--R--S | ||
| + | |||
| + | <span style="margin-left:2em;">Using these altered alphabets, we must locate the position of the letters "D", "O", and "G" in each one.</span> | ||
| + | |||
| + | 1--2--3--4--5--6--7--8--9--10-11-12-13-14-15-16-17-18-19-20-21-22-23-24-25-26 | ||
| + | C--<b>D</b>--E--F--G--H--I--J--K--L--M--N--O--P--Q--R--S--T--U--V--W--X--Y--Z--A--B - <span class="vip2">2</span> | ||
| + | A--B--C--D--E--F--G--H--I--J--K--L--M--N--<b>O</b>--P--Q--R--S--T--U--V--W--X--Y--Z - <span class="vip2">15</span> | ||
| + | T--U--V--W--Z--Y--Z--A--B--C--D--E--F--<b>G</b>--H--I--J--K--L--M--N--O--P--Q--R--S - <span class="vip2">14</span> | ||
| + | |||
| + | <span style="margin-left:2em;">These numbers are then applied to the normal alphabet to uncover the final solution.</span> | ||
| + | |||
| + | 1--<span class="vip">2</span>--3--4--5--6--7--8--9--10-11-12-13-<span class="vip2">14</span> <span class="vip3">15</span>-16-17-18-19-20-21-22-23-24-25-26 | ||
| + | A--<span class="vip">B</span>--C--D--E--F--G--H--I--J--K--L--M--<span class="vip2">N</span>--<span class="vip3">O</span>--P--Q--R--S--T--U--V--W--X--Y--Z | ||
| + | |||
| + | <b>BON</b> | ||
| + | <br /> | ||
| + | </poem></div> | ||
| + | <div class="summary" style="background-color:black;"> | ||
| + | <ul style="margin-top: 0px;"> | ||
| + | <li> | ||
| + | <div class="articleimg" style="float:right; margin: 1em; margin-top: 1em; margin-right:0px;"><html><a href="http://johnisdead.withinhubris.com/images/e/e7/Vigchart.gif" target="_blank"><img src="http://johnisdead.withinhubris.com/images/e/e7/Vigchart.gif" alt="" /></a></html><p style="margin-bottom:0px; text-align:left;"><i>A chart used for manually solving Vigenere ciphers.</i></p></div><b>Identify</b>: Text or sentences that often use proper capitalization and grammar but consist of garbled text. Difficult to discern from Caesar ciphers and keyed Caesar ciphers. Some guesswork between the two may be required. Vigenere ciphers have more unnatural letter placement than Caesar ciphers, such as three or more of the same letter appearing in a row. | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tool</b>: Any basic Vigenere translator - [http://rumkin.com/tools/cipher/vigenere.php Link] | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: Vigenere ciphers are often mistaken for Caesar ciphers, which makes them quite troublesome. One way to differenciate the two is letter placement. In Caesar ciphers, it is very unlikely that three or more of the same letter will appear in a row. This is because Caesar ciphers use a single shifted alphabet for the entire encoded message and the word structure remains untouched. However, since each letter in a Vigenere cipher uses its own shifted alphabet, more unnatural letter placement and word structure is possible. | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: Vigenere ciphers can only be solved with a key. Just like with keyed Caesar ciphers, if you encounter a seemingly unsolvable cipher consisting of garbled text, search for hints of any related or notable words or phrases. | ||
</li> | </li> | ||
<li> | <li> | ||
| − | <b> | + | <b>Tip</b>: If a key is shorter than the ciphered message, the key will simply continuously loop. For example, let's use the cipher "JOHN" and the key "ID". The letters "J" and "O" in the cipher would use alphabets beginning with the letters "I" and "D". The key would then loop back around for the next two letters, meaning the letters "H" and "N" in the cipher would also use the letters "I" and "D" respectively. |
</li> | </li> | ||
</ul> | </ul> | ||
</div> | </div> | ||
| + | <br /> | ||
| + | <h3>Keyed Vigenere Ciphers</h3> | ||
| + | <div class="fadediv2"></div> | ||
| + | <p><b>Keyed Vigenere ciphers</b> are Vigenere ciphers that have been further obfuscated by a second key or phrase. Keyed Vigenere ciphers complicate matters by altering the base alphabet used to coordinate positions between the Vigenere's key and cipher, meaning that this cipher requires two keys to solve.</p> | ||
| + | |||
| + | <div class="textexampletitle"> | ||
| + | <p style="padding-left: 1em; padding-bottom: 0.5em; color: yellow; margin-bottom: 0px;">Keyed Vigenere Cipher Examples</p> | ||
| + | </div> | ||
| + | <div class="textexamplebox"><poem style="margin-top: 0px; padding-top: 10px;"> | ||
| + | <span class="solution">Alphabet Key:</span> "JOHN" | ||
| + | <span class="solution">Key:</span> "CAT" | ||
| + | <span class="solution">Cipher:</span> "DOG" | ||
| + | |||
| + | <b style="margin-left:2em;">Answer:</b> <span class="solution">OXR</span> | ||
| + | <b style="margin-left:2em;">Solution:</b> Solve cipher through any basic Keyed Vigenere translator using the key "CAT" and the alphabet key "JOHN". | ||
| + | |||
| + | <b style="margin-left:2em;">Explanation:</b> This cipher uses an altered alphabet that begins with the provided key - "JOHN". | ||
| + | 1--2--3--4--5--6--7--8--9--10-11-12-13-14-15-16-17-18-19-20-21-22-23-24-25-26 | ||
| + | <b>J</b>--<b>O</b>--<b>H</b>--<b>N</b>--A--B--C--D--E--F--G--I--K--L--M--P--Q--R--S--T--U--V--W--X--Y--Z | ||
| + | <span style="margin-left:2em;">Each letter in the cipher "DOG" uses its own version of this altered alphabet that begins with the corresponding letter in the key "CAT". | ||
| + | |||
| + | 1--2--3--4--5--6--7--8--9--10-11-12-13-14-15-16-17-18-19-20-21-22-23-24-25-26 | ||
| + | <b>C</b>--D--E--F--G--I--K--L--M--P--Q--R--S--T--U--V--W--X--Y--Z--J--O--H--N--A--B | ||
| + | <b>A</b>--B--C--D--E--F--G--I--K--L--M--P--Q--R--S--T--U--V--W--X--Y--Z--J--O--H--N | ||
| + | <b>T</b>--U--V--W--X--Y--Z--J--O--H--N--A--B--C--D--E--F--G--I--K--L--M--P--Q--R--S | ||
| + | |||
| + | <span style="margin-left:2em;">Using these altered alphabets, we must locate the position of the letters "D", "O", and "G" in each one.</span> | ||
| + | |||
| + | 1--2--3--4--5--6--7--8--9--10-11-12-13-14-15-16-17-18-19-20-21-22-23-24-25-26 | ||
| + | C--<b>D</b>--E--F--G--I--K--L--M--P--Q--R--S--T--U--V--W--X--Y--Z--J--O--H--N--A--B - <span class="vip2">2</span> | ||
| + | A--B--C--D--E--F--G--I--K--L--M--P--Q--R--S--T--U--V--W--X--Y--Z--J--<b>O</b>--H--N - <span class="vip2">24</span> | ||
| + | T--U--V--W--X--Y--Z--J--O--H--N--A--B--C--D--E--F--<b>G</b>--I--K--L--M--P--Q--R--S - <span class="vip2">18</span> | ||
| + | |||
| + | <span style="margin-left:2em;">These numbers are then applied to the normal alphabet to uncover the final solution.</span> | ||
| + | |||
| + | 1--<span class="vip">2</span>--3--4--5--6--7--8--9--10-11-12-13-14-15-16-17-<span class="vi3">18</span>-19-20-21-22-23-<span class="vi2">24</span>-25-26 | ||
| + | J--<span class="vip">O</span>--H--N--A--B--C--D--E--F--G--I--K--L--M--P--Q--<span class="vip">R</span>--S--T--U--V--W--<span class="vip2">X</span>--Y--Z | ||
| + | |||
| + | <b>OXR</b> | ||
| + | <br /> | ||
| + | </poem></div> | ||
| + | <div class="summary" style="background-color:black;"> | ||
| + | <ul style="margin-top: 0px;"> | ||
| + | <li> | ||
| + | <b>Identify</b>: Long strings of text consisting of capitalized letters and the numbers two through seven. Contains no spaces. | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tool</b>: Any basic base32 translator - [https://paulschou.com/tools/xlate/ Link] | ||
| + | </li> | ||
| + | <li> | ||
| + | <b>Tip</b>: Base32 follows a strict character set. If you are having trouble solving a base32 cipher, make sure that there are no lower-case letters, spaces, or instances of the numbers zero, one, eight, or nine. Also ensure that your entire code is on a single line, as your base32 translator may be interpreting the line break as a character within the code. | ||
| + | </li> | ||
| + | </ul> | ||
</div> | </div> | ||
| + | <br /> | ||
| + | </div> | ||
| + | </div> | ||
| + | <div class="summary"> | ||
| + | <ul style="margin-top: 0px; padding-top: 0.5em;"> | ||
| + | <li> | ||
| + | Click "<b>Expand</b>" for a guide covering various text-based ciphers. | ||
| + | </li> | ||
| + | </ul> | ||
| + | </div> | ||
| + | <br /> | ||
| + | |||
<h2>Character Interaction</h2> | <h2>Character Interaction</h2> | ||
<h2>Analyzing Files</h2> | <h2>Analyzing Files</h2> | ||
Latest revision as of 10:48, 19 September 2024
This page covers various methods used by the Players to participate in Johnisdead.
Exploring Websites
Most of the time playing Johnisdead is spent exploring Websites. Some websites such as Lunarchildren.com contain pages of text detailing in-game lore that must be parsed through. Other sites such as Johnisdead.com consist of cryptic images and sounds that contain hints that lead to hidden pages. These hidden pages often lead to even more secret pages that reveal details important to understanding the story of Johnisdead. These long sequences of hidden pages are often referred to as Holes.
When exploring websites, it's important to check the following:
Page Source
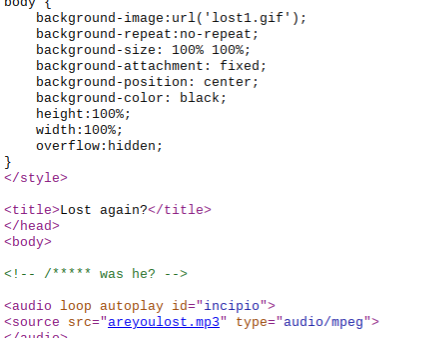
The source code of a page on Johnisdead.com referencing the page's title, image and audio files, and a hidden comment.
Most browsers have the option view the source of any web-page on the internet. This will reveal the page's HTML as loaded by your browser. Viewing a page's HTML will not only allow you to easily view secret links and filenames, but it will also reveal comments - text hidden within a page's source code. Viewing a page's source is also the easiest way to uncover the names and details of any scripts referenced on the page.
Page Title
The page title is the text that appears within your browser's tabs, favorites, and history. These titles often contain hints or ciphers that should be documented.
Files
Most pages will contain image and audio files. Accessing these files through the page source is beneficial not only for documentation purposes, but also because said files may not be fully implemented into a page. For example, a page may be scripted to only play the first five seconds of a ten second audio file. Accessing the page's files directly will reveal any hidden details. Analyzing files further will be covered in more detail further down.
Solving Ciphers
Nearly every aspect of Johnisdead's gameplay will at some point involve ciphers. Ciphers are coded messages that must be translated in a specific way to solve. There are a multitude of different ciphers, each requiring their own methods to solve:
Ascii / Decimal Based Cipher Guide
Binary Ciphers
Binary ciphers are series of ones and zeros in groups of eight. Every letter, number, and punctuation mark has a specific binary code that it is represented by. For example, the capitalized letter "A" is referenced by the binary code "01000001". The number one is referenced by the binary code "00110001". Sometimes entire sentences are encoded in binary, resulting in long blocks of binary code.
Binary Cipher Examples
01000010 01100001 01110011 01101001 01100011 00100000 01000010 01101001 01101110 01100001 01110010 01111001
Answer: Basic Binary
Solution: Solve cipher through any basic binary translator.
10011110 01001110 10000110 01110110 10010110 01000010 00000100 00100110 10100110 11001110 01001110 10100110 01101110 10100110 01001010
Answer: Reversed Binary
Solution: Reverse the cipher and solve.
ABABAABA ABBAABAB ABBBAAAA ABBABBAA ABBAAAAB ABBAAABB ABBAABAB ABBAABAA AABAAAAA ABAAAABA ABBABAAB ABBABBBA ABBAAAAB ABBBAABA ABBBBAAB
Answer: Replaced Binary
Solution: Replace the letters "A" and "B" with zeroes and ones respectively and solve.
- Identify: Groups of eight characters consisting of either ones or zeroes.
- Tool: Any basic binary translator - Link
- Tip: Binary representing common characters begin with the number zero. If you encounter binary that begins with the number one, it's likely that the entire cipher has been reversed. In this case, one must correct the cipher by reversing it themselves for it to be solved.
- Tip: As its name implies, binary's most defining trait is its use of only two characters. This makes it easily identifiable. You may encounter some binary ciphers where the ones and zeroes have been replaced with letters or even entire words. If you encounter a strange looking cipher consisting of patters such as "ABAAAAAB", its likely an obscured binary cipher.
Octal Ciphers
Octal ciphers are fairly similar to binary ciphers. Both ciphers consist of numbers and often appear in groups of eight. However, octal is a bit more complicated than binary. Octal is the "base-8" number system, meaning it uses combinations of the numbers zero through seven to represent characters.
Octal Cipher Examples
20460563 32261440 23661564 302660
Answer: Basic Octal
Solution: Solve cipher through any basic octal translator.
066203 46516632 04026213 36117213 66526442
Answer: Reversed Octal
Solution: Reverse the cipher and solve.
- Identify: Groups of numbers ranging from zero to seven. These groups never exceed eight characters. Unlike binary, these groups may contain less than eight characters.
- Tool: Any basic octal translator - Link
- Tip: The maximum amount of numbers that may appear in an octal cipher before a space appears is eight. This makes octal ciphers fairly easy to identify. If you encounter a cipher consisting of eight numbers followed by a smaller group of numbers, then it is likely an octal cipher. Example: "23240524 250".
- Tip: The numbers within an octal cipher never exceed seven. If you see numbers higher than seven in a cipher, then it is not an octal code.
Hexadecimal Ciphers
Hexadecimal ciphers are fairly easy to identify. Whereas binary and octal ciphers were both made up of groups of eight characters, hexadecimal ciphers are made up of groups of two characters. These two characters will either be two numbers, or a number followed by a letter. While octal uses a "base-8" system, hexadecimal uses a "base-16" system. This means that hexadecimal uses 16 characters - the numbers zero through nine and the letters "A" through "F".
Hexadecimal Cipher Examples
42 61 73 69 63 20 48 65 78 61 64 65 63 69 6d 61 6c
Answer: Basic Hexadecimal
Solution: Solve cipher through any basic hexadecimal translator.
c6 16 d6 96 36 56 46 16 87 56 84 02 46 56 37 27 56 67 56 25
Answer: Reversed Hexadecimal
Solution: Reverse the cipher and solve.
- Identify: Groups of two characters consisting of either two numbers or a number followed by a letter. Only the numbers zero through nine and the letters "A" through "F" are used.
- Tool: Any basic hexadecimal translator - Link
- Tip: Hexadecimal is a very distinct code. If you encounter any oddities such as groups of three characters or numbers and letters outside of the hexadecimal range, then the code has either been tampered or is a completely different cipher completely.
Base32 Ciphers
As the name implies, Base32 ciphers utilize the "base-32" system. This means that Base32 ciphers will only ever contain the following 32 characters - the capitalized letters "A" through "Z" and the numbers two through seven. Base32 ciphers contain no spaces. This makes them fairly easy to identify, as they often appear as long, uninterrupted blocks of text consisting of numbers and capitalized letters.
Base32 Cipher Examples
IJQXG2LDEBBGC43FGMZA
Answer: Basic Base32
Solution: Solve cipher through any basic Base32 translator.
SZMKWZFMCCIIWSNOSLZMXSJK
Answer: Reversed Base32
Solution: Reverse the cipher and solve.
- Identify: Long strings of text consisting of capitalized letters and the numbers two through seven. Contains no spaces.
- Tool: Any basic base32 translator - Link
- Tip: Base32 follows a strict character set. If you are having trouble solving a base32 cipher, make sure that there are no lower-case letters, spaces, or instances of the numbers zero, one, eight, or nine. Also ensure that your entire code is on a single line, as your base32 translator may be interpreting the line break as a character within the code.
Base64 Ciphers
Base64 ciphers utilize the "base-64" system, meaning they may consist of any letter, upper and lower-case, and any number. Base64 ciphers may also include the characters "/" and "+". Base64 ciphers sometimes end with one or two equal signs. There are also no spaces in Base64 ciphers, making them distinct blocks of what initially appears to be garbled letters and numbers.
Base64 Cipher Examples
QmFzaWMgQmFzZTY0
Answer: Basic Base64
Solution: Solve cipher through any basic Base64 translator.
TW9yZSBCYXNlNjQgQ29kZQ==
Answer: More Base64 Code
Solution: Solve cipher through any basic Base64 translator.
=UGZvNEI0YTZzFmQgQWZzJXZ2VmU
Answer: Reversed Base64 Code
Solution: Reverse the cipher and solve.
- Identify: Long strings of text consisting of upper and lower-case letters, numbers, and the characters "/" and "+". Often ends with one or two equal signs.
- Tool: Any basic base64 translator - Link
- Tip: Unlike previous ciphers, base64 contains all letters and numbers. This in and of itself makes it fairly easy to identify.
- Tip: The equal signs that sometimes appear within base64 ciphers always appear at the end of the code. If you encounter a cipher with one or two equal signs at the beginning of the text, it's likely this is a base64 cipher that has been reversed.
Ascii85 Ciphers
Ascii85 ciphers utilize the "base-85" system. As you might expect, this means that Ascii85 codes consist of 85 different characters. The characters used in Ascii85 ciphers are the Ascii characters 33 through 117. What this means exactly is that Ascii85 ciphers will contain every upper-case letter, every number, a plethora of punctuation marks and symbols such as "#" and "$", and the lower-case letters "a" through "u". Despite their intimidating appearance, Ascii85 ciphers can be solved the same as any other.
Ascii85 Cipher Examples
6=FqL@j"'Y@qfX:2#
Answer: Basic Ascii85
Solution: Solve cipher through any basic Ascii85 translator.
9lG&`+@C'aE,95u@<?'k+@1'YBk]Oa
Answer: More Complicated Ascii85
Solution: Solve cipher through any basic Ascii85 translator.
aO]kBY'1@+&fYcE_#tI;
Answer: Reversed Ascii85 Code
Solution: Reverse the cipher and solve.
- Identify: Long, chaotic strings of text consisting of any upper-case letter, any number, a myriad of symbols, and any lower-case letter from "a" through "u".
- Tool: Any basic Ascii85 translator - Link
- Tip: Ascii85 ciphers are incredibly chaotic, containing many different characters. This makes them easy to identify.
- Tip: Ascii85 ciphers are often found split between multiple lines. If you encounter multiple lines of Ascii85 code that is translating incorrectly, you may need to place the separate codes on one single line.
- Tip: There is no easily discernible way to tell if an Ascii85 cipher has been reversed or not. Unfortunately, a fair amount of experimentation may be required to solve some Ascii85 ciphers.
Decimal / Character / Ascii Ciphers
Decimal ciphers hide messages by directly referencing the Ascii value of each encoded character. Every character has an Ascii value attached to it often referred to as a decimal. Decimal ciphers simply consist of the values of each character of the encoded message separated by a space.
Decimal Cipher Examples
66 97 115 105 99 32 68 101 99 105 109 97 108
Answer: Basic Decimal
Solution: Solve cipher through any basic Decimal translator.
801 79 901 501 99 101 86 23 001 101 511 411 101 811 101 28
Answer: Reversed Decimal
Solution: Reverse the cipher and solve.
- Identify: One, two, or three digit numbers separated by spaces. Decimal ciphers contain no letters and only span from the number zero to 127.
- Tool: Any basic Decimal translator - Link
- Tip: Decimal ciphers look fairly similar to hexadecimal ciphers. The main difference between the two is that decimal ciphers lack letters.
- Tip: Because 127 is the maximum valid ascii value, decimal ciphers will not contain numbers above 127. If any number above this is encountered in a cipher, the cipher is either decimal code that needs to be reversed, a decimal cipher that has been tampered with, or a completely different cipher completely.
- Click "Expand" for a guide covering various Ascii and Decimal-based ciphers.
Text Based Cipher Guide
Caesar Ciphers
Caesar shifts are simple ciphers that consist of messages written with altered alphabets. The alphabets used in Caesar ciphers have different starting points depending on the shift used. For example, a Caesar shift of zero would use our normal alphabet beginning with "A", whereas a Caesar shift of five would use an alphabet that begins with the letter "F".
Caesar Cipher Examples
Gfxnh Hfjxfw Hnumjw
Answer: Basic Caesar Cipher
Solution: Solve cipher through any basic Caesar translator.
wjmunH wfxjfH ijxwjajW
Answer: Reversed Caesar Cipher
Solution: Reverse the cipher and solve.
- Identify: Text or sentences that often use proper capitalization and grammar but consist of garbled text.
- Tool: Any basic Caesar translator - Link
- Tip: There's no easy way of discerning which shift a Caesar cipher is using. The best way to solve a Caesar cipher is to type them into a Caesar cipher translator and cycle through the different shifts to discover the correct one.
- Tip: Some Caesar ciphers are reversed. This can make solving them tricky as it will be more difficult to notice the translated words once the correct shift is uncovered. If you notice any oddities within the Caesar cipher such as punctuation appearing at the beginning of sentences or capitalized letters appearing at the end, the cipher is most likely reversed.
Keyed Caesar Ciphers
Keyed Caesar ciphers are Caesar ciphers that have had their shifted alphabets further altered by a keyword or phrase. The key used in keyed Caesar ciphers is placed at the front of the alphabet. For example, an alphabet with no shifts using the key "JID" would be "JIDABCEFGHKLMN (...)". The shift is then applied to these keyed alphabets, making them nearly impossible to solve through simple guesswork.
Keyed Caesar Cipher Examples
Rglojb Ibxba Ykbrkq
Answer: Simple Keyed Caesar
Solution: Shift the Caesar cipher by zero and use the key "KEY".
Oezyxqi Wqjqp Omqcmb
Answer: Complex Keyed Caesar
Solution: Shift the Caesar cipher by 13 and use the key "KEY".
- Identify: The same as regular Caesar ciphers - words or sentences usually containing correct punctuation and grammar consisting of gibberish. Distinguishable from normal Caesar ciphers simply in the fact that they cannot be solved from shifts alone, requiring a key.
- Tool: Any basic keyed Caesar translator - Link
- Tip: Brute-forcing a keyed Caesar cipher is incredibly difficult. When encountering a difficult keyed Caesar cipher, search for any nearby clues or relevant words that may be used as a key.
Vigenere Ciphers
Vigenere ciphers can be thought of as a more complicated from of Caesar ciphers. While Caesar ciphers used a single shifted alphabet, Vigenere ciphers are encoded with multiple alphabets with varying starting positions. The starting position of these alphabets are determined by a keyword or phrase, with each letter in the key being the starting letter used for the alphabets of each letter in the cipher. Vigenere ciphers are more easily explained through example:
Vigenere Cipher Examples
Key: "CAT"
Cipher: "DOG"
Answer: BON
Solution: Solve cipher through any basic Vigenere translator using the key "CAT".
Explanation: Each letter in the cipher "DOG" uses its own alphabet that begins with the corresponding letter in the key "CAT".
1--2--3--4--5--6--7--8--9--10-11-12-13-14-15-16-17-18-19-20-21-22-23-24-25-26
C--D--E--F--G--H--I--J--K--L--M--N--O--P--Q--R--S--T--U--V--W--X--Y--Z--A--B
A--B--C--D--E--F--G--H--I--J--K--L--M--N--O--P--Q--R--S--T--U--V--W--X--Y--Z
T--U--V--W--Z--Y--Z--A--B--C--D--E--F--G--H--I--J--K--L--M--N--O--P--Q--R--S
Using these altered alphabets, we must locate the position of the letters "D", "O", and "G" in each one.
1--2--3--4--5--6--7--8--9--10-11-12-13-14-15-16-17-18-19-20-21-22-23-24-25-26
C--D--E--F--G--H--I--J--K--L--M--N--O--P--Q--R--S--T--U--V--W--X--Y--Z--A--B - 2
A--B--C--D--E--F--G--H--I--J--K--L--M--N--O--P--Q--R--S--T--U--V--W--X--Y--Z - 15
T--U--V--W--Z--Y--Z--A--B--C--D--E--F--G--H--I--J--K--L--M--N--O--P--Q--R--S - 14
These numbers are then applied to the normal alphabet to uncover the final solution.
1--2--3--4--5--6--7--8--9--10-11-12-13-14 15-16-17-18-19-20-21-22-23-24-25-26
A--B--C--D--E--F--G--H--I--J--K--L--M--N--O--P--Q--R--S--T--U--V--W--X--Y--Z
BON
- Identify: Text or sentences that often use proper capitalization and grammar but consist of garbled text. Difficult to discern from Caesar ciphers and keyed Caesar ciphers. Some guesswork between the two may be required. Vigenere ciphers have more unnatural letter placement than Caesar ciphers, such as three or more of the same letter appearing in a row.
- Tool: Any basic Vigenere translator - Link
- Tip: Vigenere ciphers are often mistaken for Caesar ciphers, which makes them quite troublesome. One way to differenciate the two is letter placement. In Caesar ciphers, it is very unlikely that three or more of the same letter will appear in a row. This is because Caesar ciphers use a single shifted alphabet for the entire encoded message and the word structure remains untouched. However, since each letter in a Vigenere cipher uses its own shifted alphabet, more unnatural letter placement and word structure is possible.
- Tip: Vigenere ciphers can only be solved with a key. Just like with keyed Caesar ciphers, if you encounter a seemingly unsolvable cipher consisting of garbled text, search for hints of any related or notable words or phrases.
- Tip: If a key is shorter than the ciphered message, the key will simply continuously loop. For example, let's use the cipher "JOHN" and the key "ID". The letters "J" and "O" in the cipher would use alphabets beginning with the letters "I" and "D". The key would then loop back around for the next two letters, meaning the letters "H" and "N" in the cipher would also use the letters "I" and "D" respectively.
Keyed Vigenere Ciphers
Keyed Vigenere ciphers are Vigenere ciphers that have been further obfuscated by a second key or phrase. Keyed Vigenere ciphers complicate matters by altering the base alphabet used to coordinate positions between the Vigenere's key and cipher, meaning that this cipher requires two keys to solve.
Keyed Vigenere Cipher Examples
Alphabet Key: "JOHN"
Key: "CAT"
Cipher: "DOG"
Answer: OXR
Solution: Solve cipher through any basic Keyed Vigenere translator using the key "CAT" and the alphabet key "JOHN".
Explanation: This cipher uses an altered alphabet that begins with the provided key - "JOHN".
1--2--3--4--5--6--7--8--9--10-11-12-13-14-15-16-17-18-19-20-21-22-23-24-25-26
J--O--H--N--A--B--C--D--E--F--G--I--K--L--M--P--Q--R--S--T--U--V--W--X--Y--Z
Each letter in the cipher "DOG" uses its own version of this altered alphabet that begins with the corresponding letter in the key "CAT".
1--2--3--4--5--6--7--8--9--10-11-12-13-14-15-16-17-18-19-20-21-22-23-24-25-26
C--D--E--F--G--I--K--L--M--P--Q--R--S--T--U--V--W--X--Y--Z--J--O--H--N--A--B
A--B--C--D--E--F--G--I--K--L--M--P--Q--R--S--T--U--V--W--X--Y--Z--J--O--H--N
T--U--V--W--X--Y--Z--J--O--H--N--A--B--C--D--E--F--G--I--K--L--M--P--Q--R--S
Using these altered alphabets, we must locate the position of the letters "D", "O", and "G" in each one.
1--2--3--4--5--6--7--8--9--10-11-12-13-14-15-16-17-18-19-20-21-22-23-24-25-26
C--D--E--F--G--I--K--L--M--P--Q--R--S--T--U--V--W--X--Y--Z--J--O--H--N--A--B - 2
A--B--C--D--E--F--G--I--K--L--M--P--Q--R--S--T--U--V--W--X--Y--Z--J--O--H--N - 24
T--U--V--W--X--Y--Z--J--O--H--N--A--B--C--D--E--F--G--I--K--L--M--P--Q--R--S - 18
These numbers are then applied to the normal alphabet to uncover the final solution.
1--2--3--4--5--6--7--8--9--10-11-12-13-14-15-16-17-18-19-20-21-22-23-24-25-26
J--O--H--N--A--B--C--D--E--F--G--I--K--L--M--P--Q--R--S--T--U--V--W--X--Y--Z
OXR
- Identify: Long strings of text consisting of capitalized letters and the numbers two through seven. Contains no spaces.
- Tool: Any basic base32 translator - Link
- Tip: Base32 follows a strict character set. If you are having trouble solving a base32 cipher, make sure that there are no lower-case letters, spaces, or instances of the numbers zero, one, eight, or nine. Also ensure that your entire code is on a single line, as your base32 translator may be interpreting the line break as a character within the code.
- Click "Expand" for a guide covering various text-based ciphers.
